Security Definition
Overview
Use Security Definition to control access to business objects across the software. Business objects refer to characteristics of fields in reports and views.
Modifications to business objects should be addressed by personnel trained in the programming of Edupoint Revelation Technology™ software.
Software Elements
The Security Access tab on the Security Definition view contains folders called Namespace folders. Each Namespace folder contains business objects related to that Namespace, and may contain additional Namespace folders.
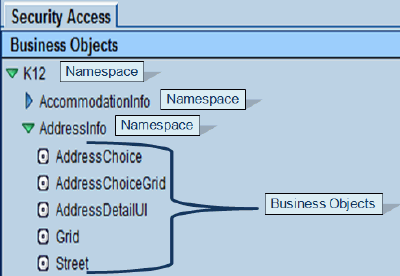
Access Inheritance
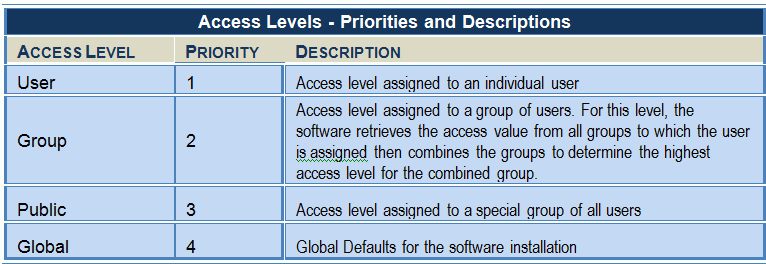
Access to business objects is defined in a logical manner. The software must gather the settings at four access levels from the lowest priority to the highest priority, then assign the access based on the access level with the highest priority.
Access Levels
Access levels include User, Group, Public, and Global. Table below describes each of four levels to which users may be assigned.
Update Field - Permissions
The Update, All Properties, Property Update fields throughout the Security Definition view contain access permissions selectable as menu options. The access permissions include: None, Update, and View. The table below describes each of these permissions
Add Field - Permissions
The Add field throughout the Security Definition view contain access permissions selectable as menu options. The access permissions include: Blank, No, and Yes. The table below describes each of these permissions.
Delete Field - Permissions
The Delete field throughout the Security Definition view contain access permissions selectable as menu options. The access permissions include: Blank, No, and Yes. The table below describes each of these permissions.
Override Field - Permissions
The Override field throughout the Security Definition view contain access permissions selectable as menu options. The access permissions include: Blank, No, and Yes. The table below describes each of these permissions.


